利用ngrok(能够将你本机的HTTP服务(站点)或TCP服务,通过部署有ngrok服务的外网伺服器暴露给外网访问)映射内网到公网,构建一个虚拟二级域名(顶级需要付费),可以进行将本地局域网被映射到公网。首先是下载ngrok,然后就是运行和简单的配置,目前支持Mac OS X 64、Windows 64位 、Linux 64位 、Linux ARM、FreeBSD 64位系统,其它我不确定,window版下载后直接运行程序即可,下面是以linux编译为例运行 ngrok help 【命令】 查看相关帮助。
首先是到官网(ngrok.com)下载相应的版本,然后在官网注册一个账号,会有一个秘钥(感觉没啥作用,不需要照样行)。然后才配置:
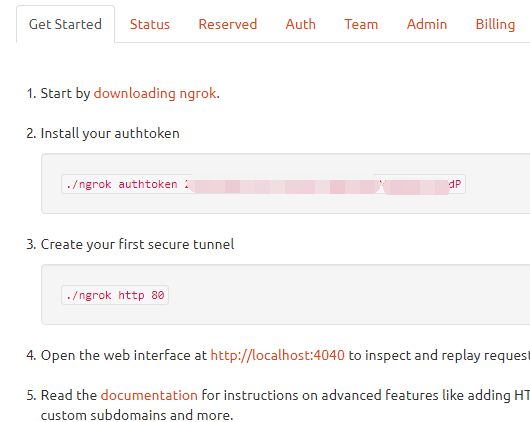
1.解压
unzip ngrok.zip
2.安装(安装目录最好是放置在/usr/local/bin/下面,这样不用配置全局变量,不过这不是非必须的)
./ngrok
3.运行
ngrok help
这是ngrok的帮助命令,通过help帮助提示可以查看我们可以做的操作,比如,开启tcp、http,以及端口设置等。
ngrok http lbc.com:80 是将本地的lbc.com映射到公网,可以通过生成的二级域名(http://99a1b18e.ngrok.io和https://99a1b18e.ngrok.io)访问,每次重启二级域名都会变化随机生成,如何要固定就要收费了。
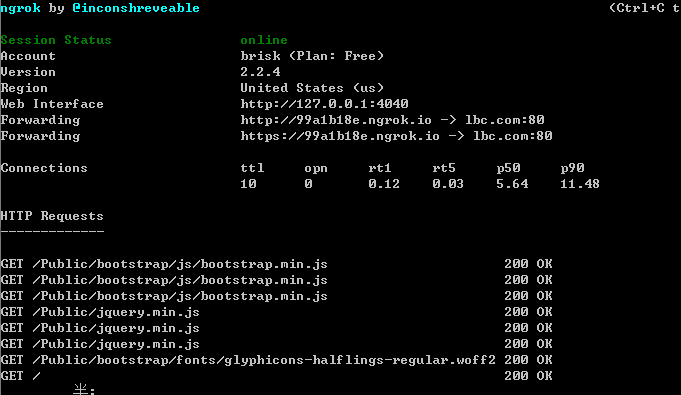
以下是一些帮助信息:
NAME:
ngrok - tunnel local ports to public URLs and inspect traffic
DESCRIPTION:
ngrok exposes local networked services behinds NATs and firewalls to the
public internet over a secure tunnel. Share local websites, build/test
webhook consumers and self-host personal services.
Detailed help for each command is available with 'ngrok help <command>'.
Open http://localhost:4040 for ngrok's web interface to inspect traffic.
EXAMPLES:
ngrok http 80 # secure public URL for port 80 web server
ngrok http -subdomain=baz 8080 # port 8080 available at baz.ngrok.io
ngrok http foo.dev:80 # tunnel to host:port instead of localhost
ngrok tcp 22 # tunnel arbitrary TCP traffic to port 22
ngrok tls -hostname=foo.com 443 # TLS traffic for foo.com to port 443
ngrok start foo bar baz # start tunnels from the configuration file
VERSION:
2.2.4
AUTHOR:
inconshreveable - <alan@ngrok.com>
COMMANDS:
authtoken save authtoken to configuration file
credits prints author and licensing information
http start an HTTP tunnel
start start tunnels by name from the configuration file
tcp start a TCP tunnel
tls start a TLS tunnel
update update ngrok to the latest version
version print the version string
help Shows a list of commands or help for one command
下面是ngrok start命令帮助
[root@localhost weibingsheng]# ngrok help start
NAME:
start - start tunnels by name from the configuration file
USAGE:
ngrok start [command options] [arguments...]
DESCRIPTION:
Starts tunnels by name from the configuration file. You may specify any
number of tunnel names. You may start all tunnels in the configuration
file with the --all switch.
EXAMPLES:
ngrok start dev # start tunnel named 'dev' in the configuration file
ngrok start web blog # start tunnels named 'web' and 'blog'
ngrok start --all # start all tunnels defined in the config file
OPTIONS:
--all start all tunnels in the configuration file
--authtoken ngrok.com authtoken identifying a user
--config path to config files; they are merged if multiple
--log "false" path to log file, 'stdout', 'stderr' or 'false'
--log-format "term" log record format: 'term', 'logfmt', 'json'
--log-level "info" logging level
--none start running no tunnels
--region ngrok server region [us, eu, au, ap] (default: us)
下面是ngrok http命令的帮助
[root@localhost weibingsheng]# ngrok help http
NAME:
http - start an HTTP tunnel
USAGE:
ngrok http [command options] [arguments...]
DESCRIPTION:
Starts a tunnel listening for HTTP/HTTPS traffic with a specific hostname.
The HTTP Host header on incoming public requests is inspected to
determine which tunnel it matches.
HTTPS endpoints terminate TLS traffic at the ngrok server using the
ngrok.io certificates. The decrypted, HTTP traffic is then forwarded
through the secure tunnel and then to your local server. If you don't want
your TLS traffic to terminate at the ngrok server, use a TLS or TCP tunnel.
EXAMPLES:
ngrok http 8080 # forward ngrok.io subdomain to port 80
ngrok http example.com:9000 # forward traffic to example.com:9000
ngrok http -subdomain=bar 80 # request subdomain name: 'bar.ngrok.io'
ngrok http -hostname=ex.com 1234 # request tunnel 'ex.com' (DNS CNAME)
ngrok http -auth='falken:joshua' 80 # enforce basic auth on tunnel endpoint
ngrok http -host-header=ex.com 80 # rewrite the Host header to 'ex.com'
OPTIONS:
--auth enforce basic auth on tunnel endpoint, 'user:password'
--authtoken ngrok.com authtoken identifying a user
--bind-tls "both" listen for http, https or both: true/false/both
--config path to config files; they are merged if multiple
--host-header set Host header; if 'rewrite' use local address hostname
--hostname host tunnel on custom hostname (requires DNS CNAME)
--inspect enable/disable http introspection
--log "false" path to log file, 'stdout', 'stderr' or 'false'
--log-format "term" log record format: 'term', 'logfmt', 'json'
--log-level "info" logging level
--region ngrok server region [us, eu, au, ap] (default: us)
--subdomain host tunnel on a custom subdomain